Unplugged from Deplatforming, Plugged into Freedom.
Sovereign solutions for DNS, CDN, WAF, and DDoS mitigation.



Global CDN
Edge servers in strategic locations provide resilience to attacks and cache content for reduced latency and improved load times.
Learn MoreFlexible DNS
In-house DNS with geo-targeting, health checks and failover records. Supports 60s TTL and changes propagate instantly.
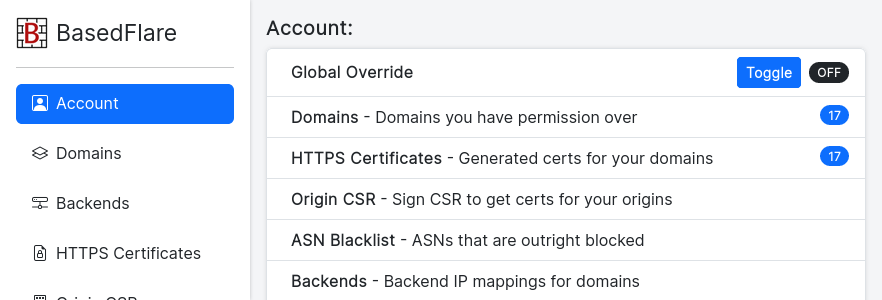
Learn MoreFeature-Rich Dashboard
Manage domains, DNS, load balancing, HTTPS certificates, black/whitelists, bot filtering & more in a single location.
Sign UpOpen Source
We believe in open source software, and maintain a public code repository with some of our backend components.
Code RepositoryNetwork Map
Pricing Plans
For early access and a free trial, contact us.
Starter
Good for smaller websites and hobbyists.
- 1 origin
- Low Traffic
- Free HTTPS certificates
- Global caching CDN
- DDoS protection
- Advanced DNS
Pro
Perfect for small / medium businesses with more traffic.
- 10 origins
- Moderate traffic
- Free HTTPS certificates
- Global caching CDN
- DDoS protection
- Advanced DNS
- Origin load balancing
Enterprise
We can accommodate just about anything and offer competitive pricing.
- All pro features
- Managed video livestreaming
- Unlimited everything
- Phone support hotline
- Custom features & consulting
- Exclusive PoPs
- Onion routed origin connections
- Censorship resistant options
Frequently Asked Questions
FAQWe believe open sourcing parts of our software improves transparency and security. Anybody in the world can look through our source code and see there are no hidden tricks, spying, or telemetry.
Furthermore, it enables the vast community of open source volunteers to directly contribute code improvements, features and bug fixes which would not be possible with locked-down proprietery software.
We allow freedom of expression. Unless compelled legally, such as by a court order, we will never discriminate customers based on website content or give in to any protest or social pressures.
We've built from the ground up to be vendor agnostic and agile. That means we don't depend on any specific "cloud" provider, and no single company can decide to take you offline, period.
If you are a high-risk and/or high-profile website facing censorship, get in touch today to discuss solutions.
Yes, invoices can be paid in various cryptocurrencies via our self-hosted payment gateway. We accept XMR, BTC, LTC, ETH, ETH-USDT and ETH-USDC.
DDoS or DoS, stands for (distributed) denial of service. This refers to a class of cyber attack which typically involves sending large amounts of fraudulent traffic to overwhelm your website or server, making it impossible to access or extremely slow for legitimate users and effectively denying service. Learn more on WikiLess.
Motivations for DDoS attacks vary but are commonly perpetrated by criminal organisations trying to extort you, or shady competitors seeking to get an unfair advantage.
Don't become a victim. BasedFlare specialises in protecting you against these kind of attacks. Our network will filter and absorb malicious traffic, passing only legitimate traffic to your backend servers and ensuring service continuity.
• DNS nameservers with advanced features (GeoDNS, health checks, failover records)
• Backend server management and load balancing
• HTTPS certificate generation and automatic renewal
• Strict HTTPS to backends with private CA signed certificates
• DDoS protection settings and rule management
• Redirects and rewrite rules
• IP/subnet blacklist and whitelist
• ASN blacklist
• Maintenance mode toggle
• Much more...
Of course! Visit basedstatus.online to see current status and uptime for all of our services.
Have a question that isn't answered here or want to know more? Contact us.